Services
Cyber Security
We ensure the security of our customers’ digital landscapes with innovative cybersecurity solutions for a zero-trust world. We help businesses enhance their cybersecurity strategies and achieve a highly effective digital transformation through our proven approach and comprehensive portfolio of cybersecurity solutions.
Cybersecurity Expertise
Our team of experienced cybersecurity professionals stays updated with the latest threats and trends, employing advanced technologies and strategies to mitigate risks and protect your organization.
Comprehensive Security Approach
We take a holistic approach to cybersecurity, considering all aspects of your organization's infrastructure, applications, and data to develop robust and multi-layered security solutions
Proactive Threat Detection
Our advanced threat detection systems and round-the-clock monitoring ensure early detection of potential security breaches, allowing for immediate response and mitigation.
Customized Security Solutions
We understand that every business has unique security requirements. Our team works closely with you to design customized security solutions that align with your specific needs and industry regulations.
Continuous Support and Maintenance
Our dedicated security team provides ongoing support, monitoring, and maintenance to ensure that your cybersecurity defenses remain strong and effective.
Managed SOC Services
PROACTIVE MONITORING
- Establishment of Automated Monitoring – SNMP.
- Configurations and categorization of Monitored Objects.
- Configurations for Automated Monitored and Object Reporting.
- Integration to Business Process.
- Automatic Assignment of Risk Level.
ALERTS AND NOTIFICATIONS
- Automation configurations for Alerts and Notifications – SNMP Trap / IF-MAP event.
- Configurations to categorize alerts based on Risk Level.
- Configurations for notifications to Business Process Owner.
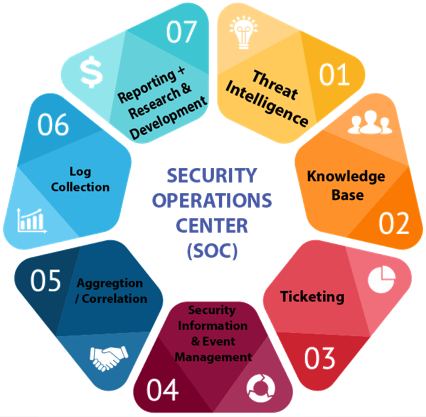
EVENT CORRELATION
- Configurations for contextual correlation of events.
- Situational awareness Mapped to Business Process.
INCIDENT RESPONSE
- To prepare workflow for Network Forensics.
- To prepare workflow for Investigation and Analysis.
- To prepare templates for Evidence Gathering.
- To prepare matrix for Escalation Management.
REPORTING
- Reporting templates building based on incidents.
- Feedback templates and Review Process building.
BEHAVIOUR ANALYSIS
- Rules and alerts configurations for Network Behavioral Analysis Detection.
- Rules and alert configurations Anomaly Detection.
- Framework establishment for Predictive Analysis.
- Creation of Business Process Profiling.
SOC Maturity & Capability Assessment
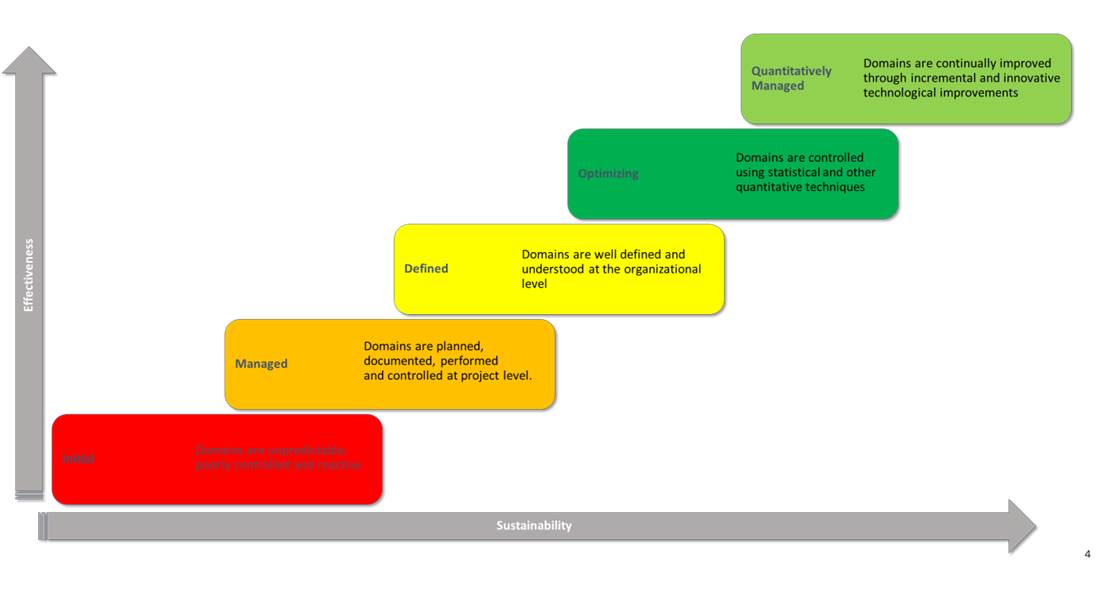
Strategic SOC Maturity Evaluation through CMM Methodology
The Capability Maturity Model (CMM) methodology serves as a foundational framework for conducting Security Operations Center (SOC) maturity assessments. This structured approach evaluates maturity levels across five key domains: business, people, process, technology, and services. By employing the CMM methodology, organizations can gain valuable insights into the effectiveness and evolution of their SOC capabilities, enabling strategic enhancements in each domain. This comprehensive assessment ensures a holistic understanding of security operations, paving the way for targeted improvements and a resilient cybersecurity posture.
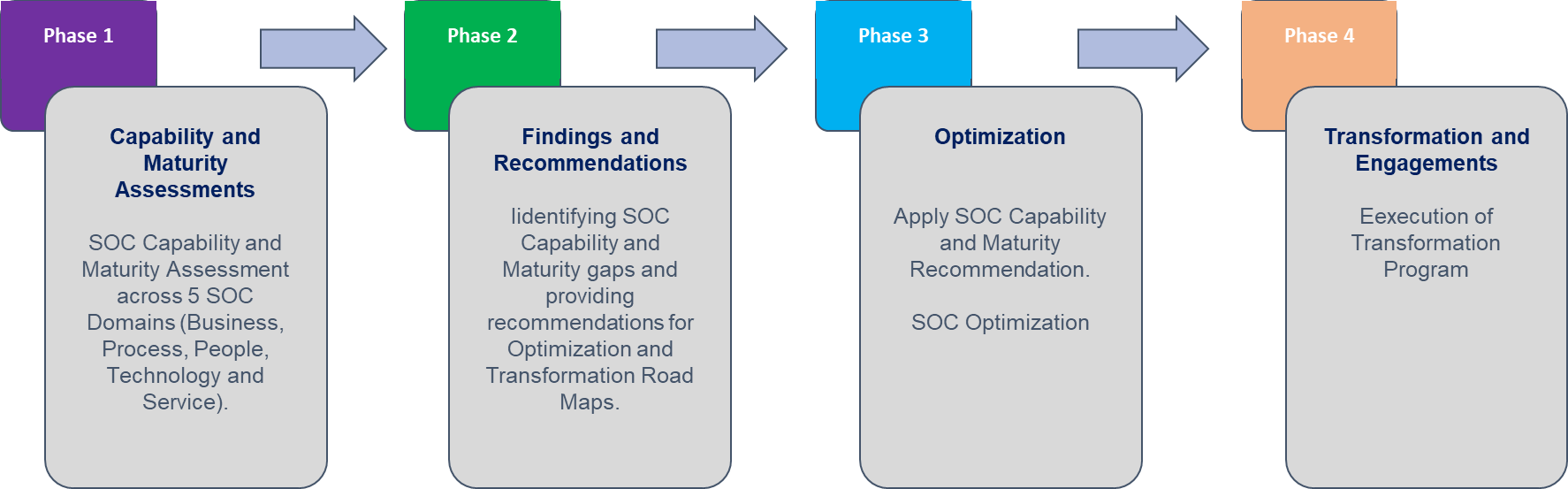
Evolutionary Phases in SOC Maturity Assessment
The SOC maturity assessment process unfolds through four integral phases. Initially, the Capability and Maturity Assessment phase lays the groundwork by evaluating the existing state across business, people, process, technology, and services domains. Subsequently, the Findings and Recommendations phase crystallizes insights gained, offering a strategic roadmap for improvement. The Optimization phase follows suit, implementing targeted enhancements based on identified areas of growth. Finally, the Transformation and Engagements phase heralds the evolution of the SOC, ensuring alignment with best practices and fostering ongoing resilience against evolving cybersecurity challenges.
Risk Assessment and security framework
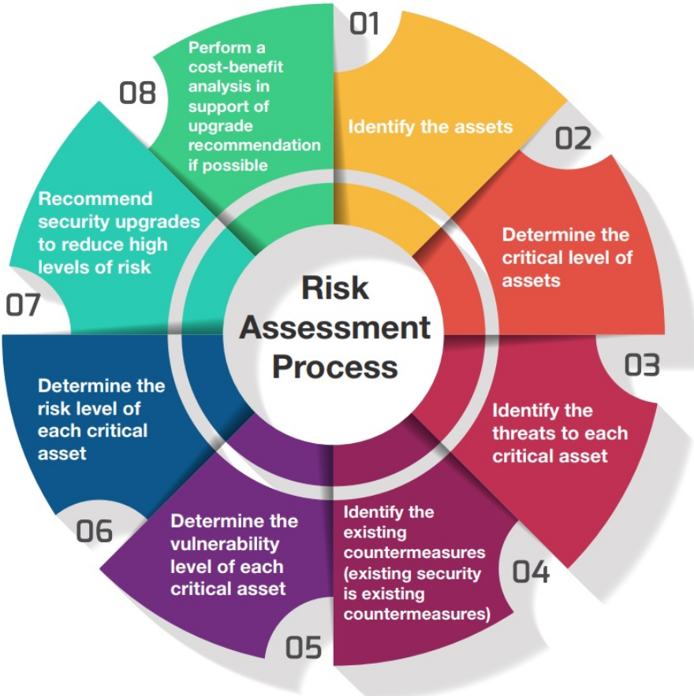
Integrated Risk Assessment and Mitigation Strategy
Assets undergo thorough characterization for risk assessment, distinguishing critical and noncritical elements to establish baselines. OCTAVE charts are then crafted, identifying threats to critical assets and evaluating existing countermeasures. Subsequent vulnerability assessments and penetration testing determine actionable steps, with resultant risk levels documented in a comprehensive register for acceptance. To mitigate high-risk scenarios, precise recommendations are provided, complemented by a detailed risk management plan. A meticulous analysis ensues, evaluating the implementation feasibility through SOPs, frameworks, or advanced technologies, fortifying the organization against potential threats.
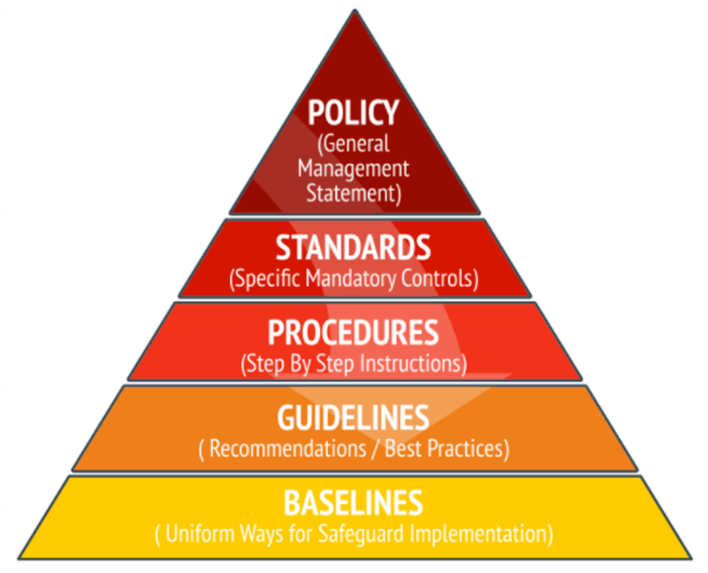
Preparing Security Framework
- Policy – Information Security Policy is a comprehensive statement made by the company’s senior management, indicating the role of security in the organization.
- Standards– mandatory actions or rules. Standards help, support, and develop policies in certain areas.
- Procedures – detailed step-by-step descriptions of tasks performed to achieve a certain goal.
- Guidelines– describe the recommended actions and operating instructions for users, IT professionals, and other staff members, when the appropriate Standards do not apply.
- Baselines– uniform ways of implementing a given safeguard. The system must meet the baseline described by benchmarks.
Penetration testing/VA testing
Security Testing
Under the umbrella of 'Security Testing,' a comprehensive approach is undertaken to fortify digital landscapes against potential threats. This includes meticulous Security Scanning, delving into the intricate details of Vulnerability Scanning, System and OS Penetration Testing, and Application Penetration Testing. The scrutiny extends to Mobile Penetration Testing, ensuring robust security measures in the dynamic mobile landscape. The process also involves Security Auditing, Ethical Hacking, and a thorough Posture Assessment. Each facet contributes to a layered defense strategy, identifying and mitigating vulnerabilities, ultimately safeguarding systems and applications from potential cyber threats.
OT CYBERSECURITY
Our OT cybersecurity services go beyond identification to proactively target vulnerabilities, devising robust solutions that shield operational technology (OT) assets. We take pride in offering top-tier advisory services, setting a benchmark for excellence.
- OT/ICS/SCADA/IOT/IIOT Cybersecurity consulting
- Cyber Security Governance
- Audit & Assessment
- Vulnerability Management
- Secure Remote Access
- Secure Architecture Design
- Cloud Security
- Cyber Security Roadmap
Unlock the Potential of Cyber Security - Contact Us Today!
Elevate Your Operations
Ready to fortify your organization's cybersecurity with state-of-the-art solutions? Connect with Technology Links Inc. now to explore how our advanced cybersecurity services can boost resilience, scalability, and performance for your business.
Let our experts assess your unique requirements and craft a customized solution perfectly aligned with your business goals. Unlock the power of advanced cybersecurity solutions with Technology Links Inc. – your trusted technology partner.
Solutions
Get In Touch
info@technology-links.com
